IDEMIA Product Security Incident Response Team (PSIRT)
We are constantly innovating and looking for ways to improve, be efficient and competitive with our products and services, security is our priority, and we always implement the highest standards to protect our customers.
IDEMIA PSIRT is the process by which IDEMIA customers, security researchers, industry groups, and government organizations or vendors report potential security vulnerabilities in IDEMIA. IDEMIA’s PSIRT team aims to reduce risk by providing information, guidance and resolution of vulnerabilities in IDEMIA products as quickly as possible.
To help protect its customers, IDEMIA does not publicly disclose or confirm security vulnerabilities until IDEMIA has conducted an analysis of the product and issued fixes and/or mitigations.
IDEMIA PSIRT manages the receipt, investigation and internal coordination of security vulnerability information related to all IDEMIA products. This team then coordinates with each individual IDEMIA product and solution team to investigate, and if needed, identify the appropriate response plan. Maintaining communication between all involved parties, both internal and external, is a key component of IDEMIA’s vulnerability response process.
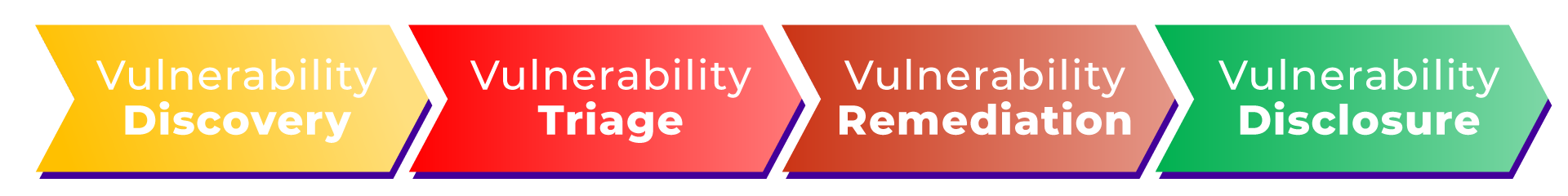
The IDEMIA PSIRT process is based on the “FIRST” framework and follows these four steps: Discovery, Triage, Remediation and Disclosure.
Report a Product Security Vulnerability on an IDEMIA Product
Before reporting a vulnerability please read the IDEMIA vulnerability disclosure policy carefully.
Report product security vulnerabilities via email to psirt@idemia.com.
Use the IDEMIA PGP public key to encrypt email in case of sensitive information.
ID: 3F 7B 38 52
Hash: 23D4 0419 536D 449A 5513 24B0 3EB5 19D9 3F7B 3852
IDEMIA PSIRT PGP Key



